The most commonly used protocol in SSH is the shell protocol. In OnTheSSH, there are multiple ways to open a shell terminal:
- Double-click a remote host name in the left sidebar
- Click on a remote host name with your mouse in the left sidebar, and then click the “shell Terminal” button on the right
- Copy an IP address to the system clipboard (for details, refer to the Convenient SSH connection section later)
At the bottom right side of the shell terminal window, there is information about function keys and the number of rows and columns:
- Ctrl+H: Open the help window
- Ctrl+T: Open the Settings window
- Lines: Display the number of lines (character height) of the shell window. When the mouse stretches the window, the number of lines will change
- Colnums: Display the number of columns (character width) of the shell window. When the mouse stretches the window, this number of columns will change
Help Window
Pressing Ctrl+H will open the help window.
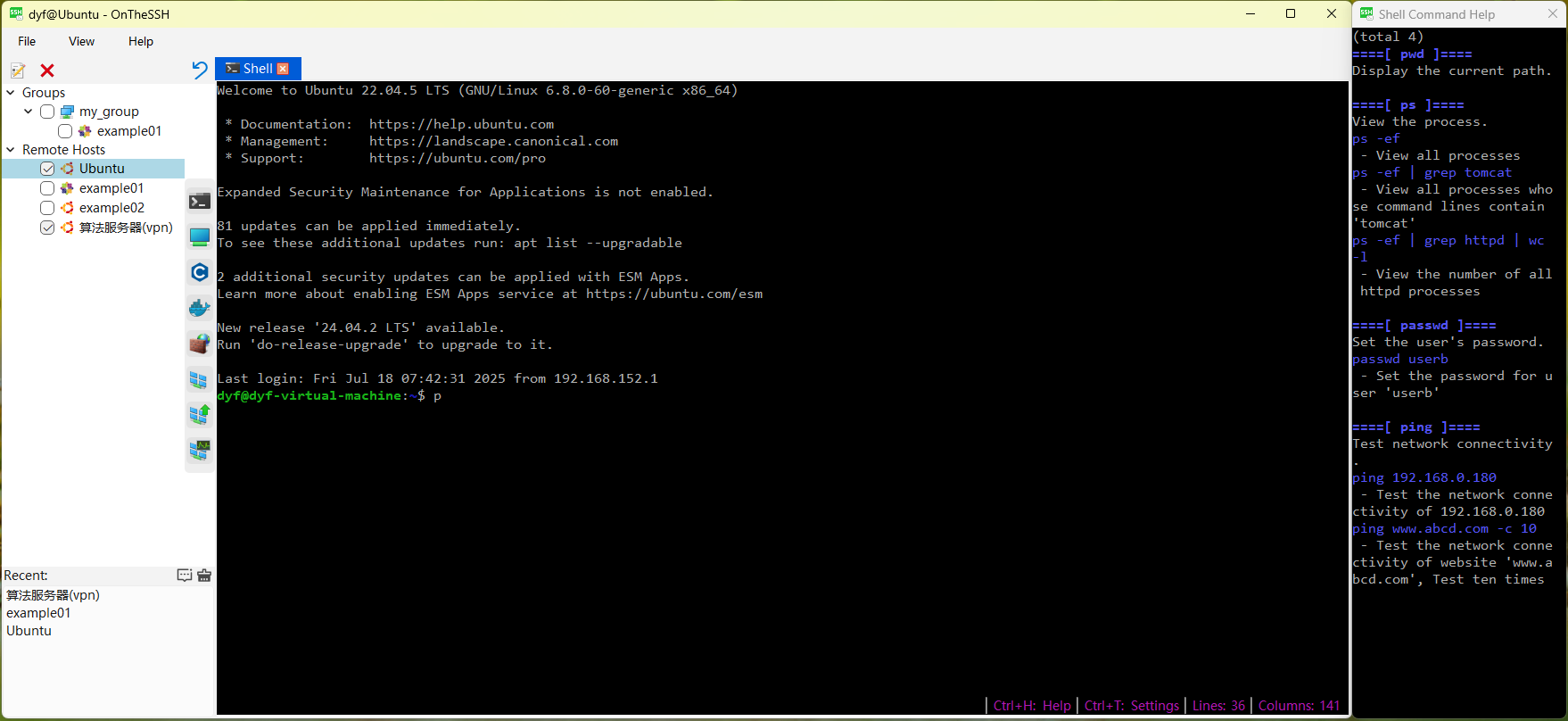
The help window will appear by default on the right side of the main window, displaying help information for commonly used shell commands. Note that the help content and the shell terminal are interrelated. For instance, if you enter the character ‘p’ in the shell terminal, the help window will automatically display several commands starting with the character ‘p’, as shown in the above figure.
Settings Window
Pressing Ctrl+T will open the Settings window.
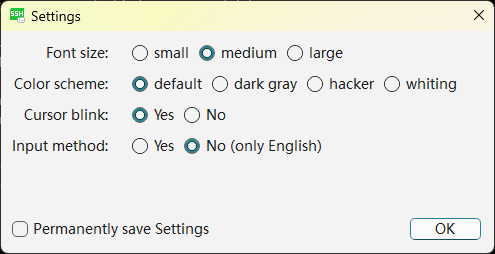
Here, you can set the size of the displayed font, color style, whether the cursor flashes, and whether input methods are supported. If you check the “Permanently Save Settings” option below, this setting will be valid when you open this remote host shell window in the future. If you don’t check it, it will only be valid in the current shell window.
Mouse
The mouse in the shell terminal has the following functions:
| Double-click | Select the word and copy the selected text to the system clipboard |
| Select (drag) | Copy the selected text to the system clipboard |
| Right-click | Paste the content of the system clipboard to the cursor position |
| Mouse wheel | Window scrolling (Ineffective when using alternate Windows such as vim programs) |
Convenient SSH connection
Under normal circumstances, to connect to a remote Linux host, you need to first create this remote host in the OnTheSSH program (in the left column). In some cases, only a temporary connection to this remote host is required. Here is a convenient method provided:
Copy the “connection information” of this remote host to the clipboard. At this point, the program will recognize this “connection information” and prompt it with a flashing icon (in the “Recent” column on the left). When you click on this flashing icon, a window will pop up to guide you through subsequent operations.

The program will automatically recognize the first “connection information” in the clipboard, which includes the following types:
- ip address, such as 192.168.2.45
- Address and port, such as 10.2.3.4:2222
- Address, port and username, such as test@127.0.0.1:800
- Address, port, username and password, such as gest#passwd@127.0.0.1:800 (when the password contains the # character, it does not affect the recognition of the information. For example, gest#1234#$%@127.0.0.1:800 can recognize that the user is gest and the password is 1234#$%)
This might be very useful for operation and maintenance personnel, who usually manage dozens or even hundreds of remote hosts and use tools like Notepad and Excel to record connection information. The convenient connection function can be adapted to their usage habits. When he wants to connect to a remote host, he can copy the connection information of that host from notepad or Excel (e.g. root@10.10.3.4:22) to the clipboard, and then click the “flashing icon” to establish the SSH connection.
In-depth SSH Protocol
The latest version (v1.7) of the shell terminal displays the “depth” information of SSH connections, which will be helpful to technicians.
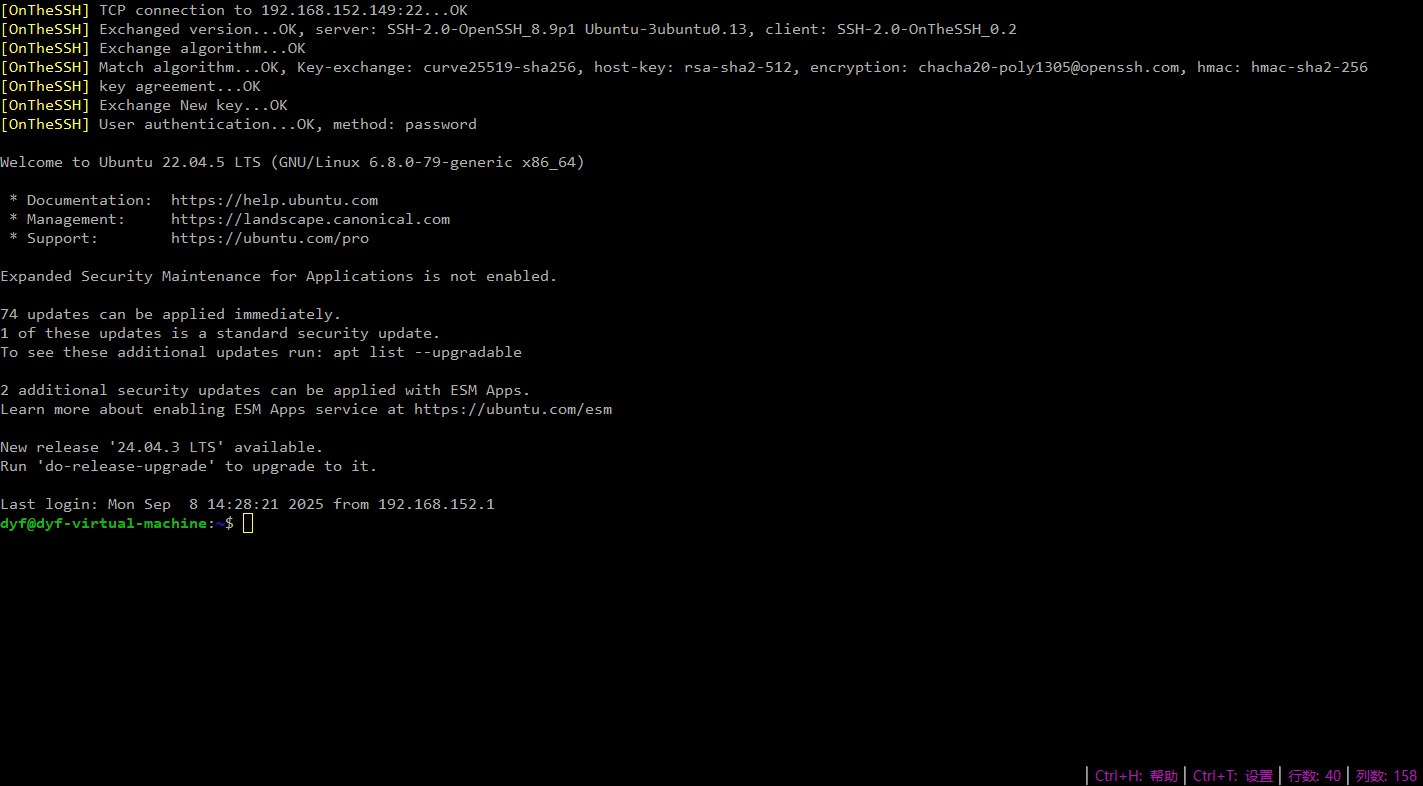
When successfully connecting to a remote host, the first few lines of the shell terminal, prefixed with [OnTheSSH], show the entire process of the SSH connection. Let’s illustrate with the above picture as an example:
- TCP connection to 192.168.152.149:22…OK — This indicates that the client (OnTheSSH software) has successfully connected to port 22 of the remote host 192.168.152.149 via TCP.
- Exchanged version…OK — This indicates a successful version exchange, which is the first step of the SSH key exchange protocol. Here, it can be seen that the server is OpenSSH_8.9 and the system is Ubuntu.
- Exchange algorithm…OK — This indicates that both parties exchange algorithms, which is the second step of the SSH key exchange protocol.
- Match algorithm…OK — It indicates that the algorithm has been determined.
- Key-exchange — The key exchange algorithm adopts ‘curve25519-sha256’
- host-key — The host key algorithm adopts ‘rsa-sha2-512’
- ecryption — The encryption algorithm is ‘chacha20-poly1305@openssh.com’
- hmac — Keyed-Hash Message Authentication algorithm is ‘hmac-sha2-256’
- Key agreement…OK — This indicates that both parties have finally determined the key of the algorithm by exchanging public keys and passed the verification. This is the third step of the SSH key exchange protocol.
- Exchange New key…OK — This indicates that both parties agree on the previous key calculation, which is the final step of the SSH key exchange protocol. All subsequent information interactions must be encrypted.
- User authentication…OK — It indicates that the user authentication was successful.
- method — Use the ‘password’ authentication method
The latest version (v1.7) has added support for older systems. Below is an example of connecting to a MacOS system that is over 10 years old, where you can see the use of some old algorithms (which have been proven to be less secure).
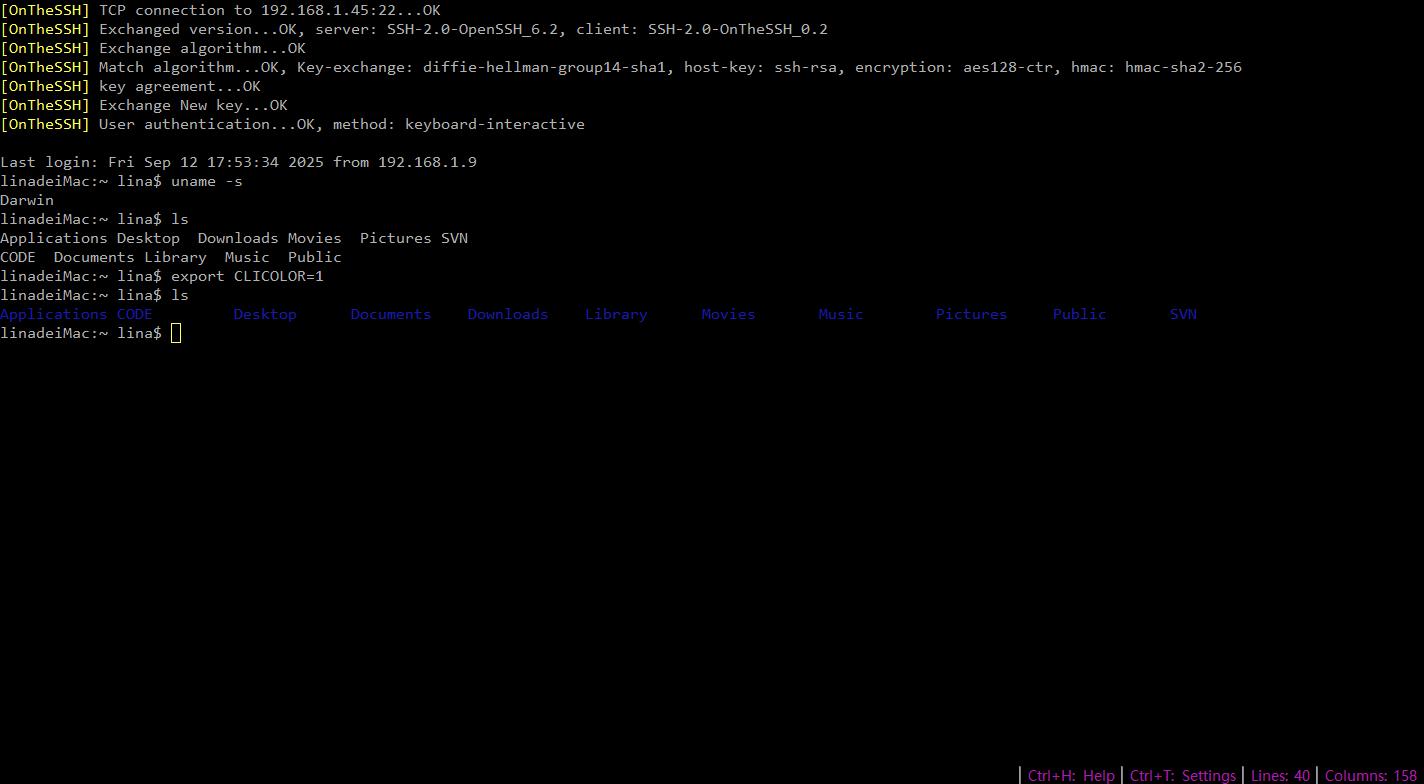
The server version is OpenSSH6.2, the key exchange algorithm is diffie-hellman-group14-sha1, and the host key algorithm is ssh-rsa. From a security perspective alone, they all need to be upgraded.
There is another difference from the previous picture. The authentication method adopts Keyboard-interactive (keyboard exchange method), indicating that the password is entered in the form of questions and answers. OnTheSSH has carried out automatic processing internally, and the final usage feels the same as the password authentication method.
Other online documents:
